Fill out the form to get more information about the Fullstack Academy bootcamp of your choice.

Scammer: “We need to repair all of the services which got broken.”
Victim: “Yep, I see that.
Scammer: “Sir, there will be a charge of £1295 [$1,609].”
Victim: “Oh, bloody hell.”
Scammer: “Hey, why are you crying, man?”
Victim: “I suffer from depression.”
Scammer: “No, no, everything will be okay. Don’t worry. Now promise me you won’t cry again, OK?” [Laughing in background]
Jim Browning—widely known in cybersecurity circles as an expert ethical hacker—was able to hack into this heart-breaking scam call, and as a result of Jim’s work, the victim was eventually reimbursed.
The conversation above was captured in Part 4 of his recent Spying on the Scammers series, a project that was so impactful that it led to a BBC documentary. We talked with Jim about his motivations and advice for those considering a career in cybersecurity.
Who Is Jim Browning?
Jim is most famous for “scamming the scammer,” whereby he uses his expert cybersecurity knowledge to break into scammers’ computers when they attempt to connect to his computer.
An important nuance is that he’s not hunting down scammers—he’s just reacting when scammers try to victimize him. According to his YouTube Channel—which has over 77 million views—he’s “tracking and identifying scammers who knock my front door, call me or shove popups onto my computer screen.”
Jim’s efforts disrupt scam call centers, which can make millions of dollars a year, so he had to keep much of his personal information private in our interview.
What did we find out about Jim? He has a “proper IT job” located in the UK. And, obviously, “Jim Browning” is not his real name. During our Skype interview, we didn’t see his face, which he politely apologized for, but according to him, “my computer doesn’t have a video camera.”
What Motivates Him?
Jim seems to have two motivations common among many working in the cybersecurity industry: the thrill of applying his technical expertise to catch a scammer as well as knowing that the work he’s doing is making the world a safer place. During our conversation, he called out two of his videos that he found especially important.
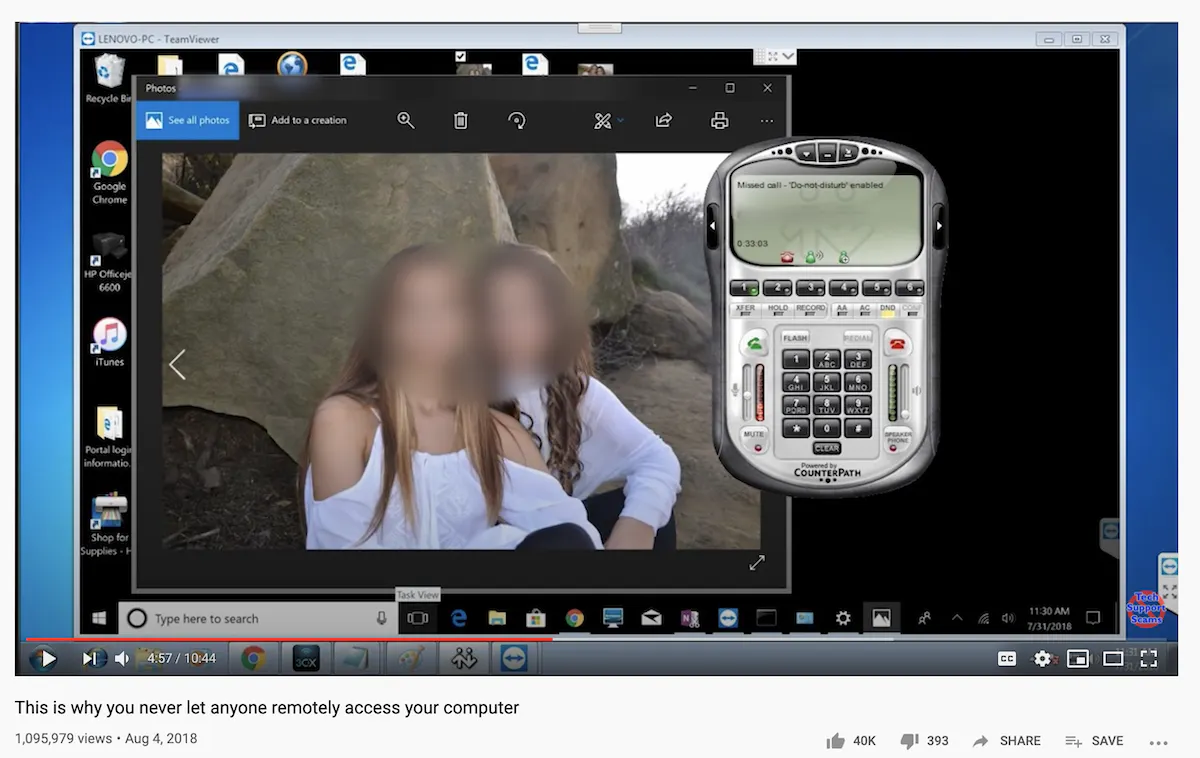
The first, "This is why you never let anyone remotely access your computer,” shows a victim who was called by a scammer claiming to be from Chase Bank.
Early in the call, the victim gave the scammer remote access to her computer. Once the scammer had control, he deleted all her files—including all the photos of her children—and used them as a bargaining tool to get more money.
Along the way, the scammer pulled up the photos and made crude comments about her family. Jim was able to disconnect the scammer’s remote access without them realizing what was happening. In Jim’s words, the video shows a victim’s “worst nightmare.”
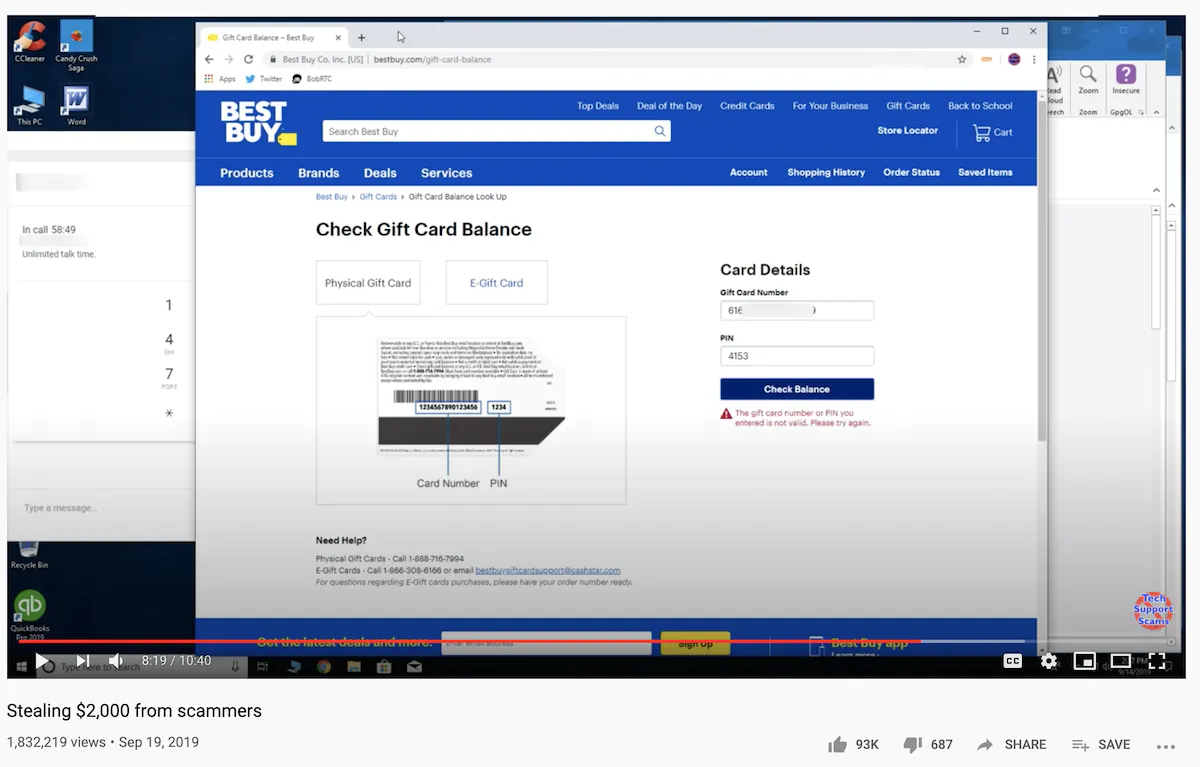
In the second video, "Stealing $2,000 from scammers,”a victim was scammed into buying $2,000 worth of Best Buy gift cards.
Through a series of creative maneuvers, Jim was able to work quickly with a helpful store representative to intercept the gift card information and slow down the process using the store pickup option. With the time saved, Jim was able to get the money refunded to the victim.
Good news stories like these are rare, unfortunately, compared to the thousands of daily scams and cybersecurity attacks that impact individuals and organizations across the globe.
Even for those Jim is able to help, the emotional impact of being victimized isn’t something he can erase.
One of his goals in sharing his work on YouTube is to educate the public and governments (including local police) to prevent these crimes from happening instead of just being intercepted.
Advice for a Career in Cybersecurity
In addition to giving us insight into his experiences, Jim also shared his advice for those who are interested in a career in cybersecurity. “Be as hands-on as possible. Try and find vulnerabilities in the system and do your best to think like an attacker.”
He added that cyber professionals should always be learning and keeping their knowledge up to date.
If you’re concerned about not having the “right” background to succeed in cybersecurity, Jim highlighted the importance of hiring cyber professionals with diverse skill sets. “If you work as a team and you all have the same background, you’ll all think alike. You should have as wide a range of people as you can get.”
Although Fullstack doesn’t support unauthorized or potentially illegal hacking, we’re strong advocates of using the power of cybersecurity to make the world a safer place. And this is only possible through a sea of individual cybersecurity experts who can combat the ever-growing, ever-evolving threats.
If you’re curious about how to start a cybersecurity career, check out our free Hacking 101, or learn about our full- or online part-time cybersecurity bootcamps.


